- How to understand the rapid changes of «smart» and «connected» cars?
- How to minimize the costs of securing your supply chain while respecting time constraints?
- How do I obtain the safety proofs of work required by UNECE regulations?
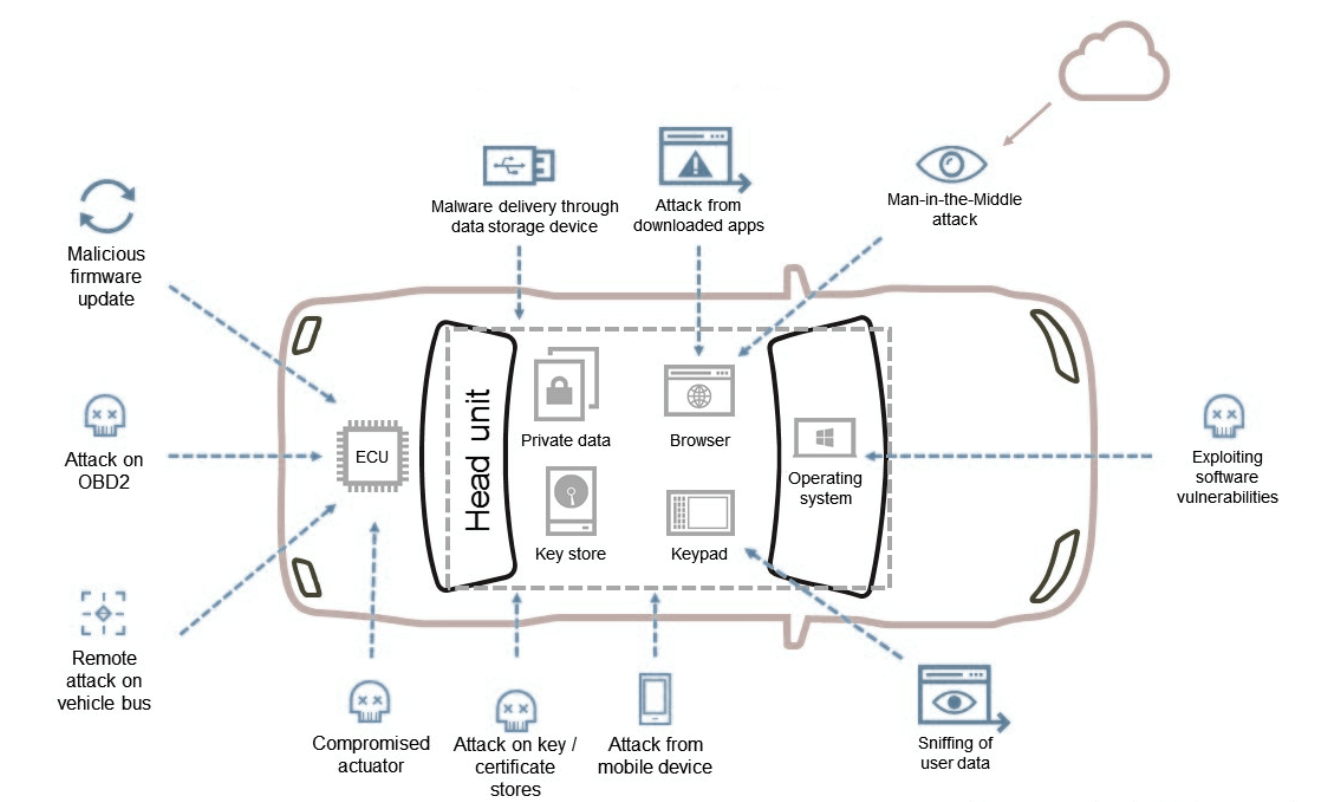
The rapid evolution of the automotive industry and the transformation of vehicles into connected objects with new services offered to the driver have put the integration of several technological solutions (hardware, software, connectivity, data management…) at the heart of innovations.
These changes increase the risk of getting security flaws. As an integrator of multiple levels of suppliers, you must master and control all the technological parts to be integrated, in order to achieve a secure connected vehicle that complies with UNECE regulations.
Talk to our experts
A security audit in the automotive industry ensures the identification and mitigation of potential threats to connected vehicles and associated systems.
This audit evaluates the robustness of cybersecurity measures, assesses compliance with automotive cybersecurity standards, and identifies vulnerabilities. Through comprehensive testing and analysis, the audit enhances the overall security posture, protecting against unauthorized access, data breaches, and potential safety risks. This proactive approach not only safeguards sensitive information but also builds trust among stakeholders, fosters compliance with regulatory requirements, and ultimately contributes to a resilient and secure automotive ecosystem.
It offers invaluable benefits by systematically assessing and enhancing connected car security overall. Moreover, our tailored and hands-on trainings provide your team with necessary knowledge and skills in order to approach the basics of automotive security.

A tripartite
relationship management
Obtain
«type approval»
Control
Costs (OpEx)
Resources