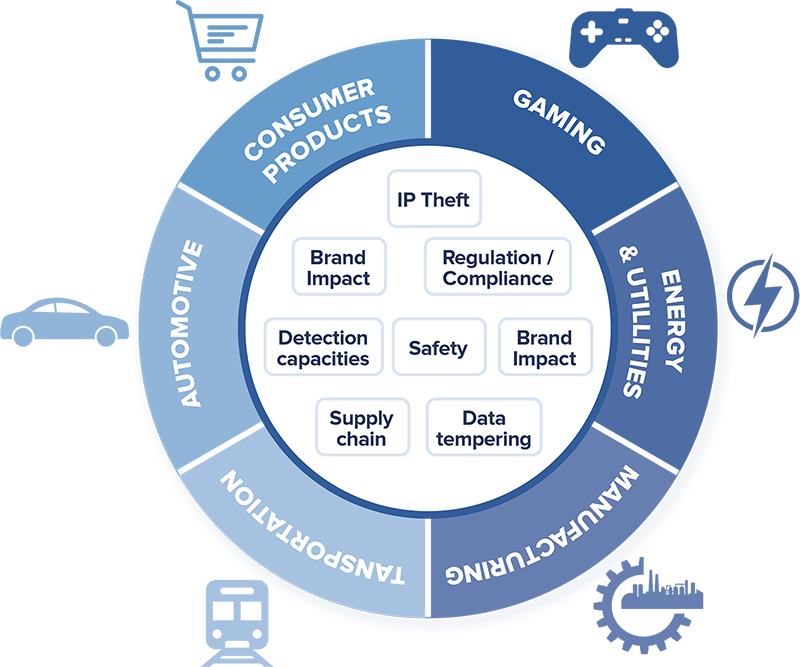
- How to prevent connected devices from being infected with malware and joining a botnet?
- How to preserve your innovations while maintaining the trust of your users?
- How to comply with the growing regulation of connected devices (Cyber Resilience Act, NIS 2, ETSI EN34343, IoT Consumer)?