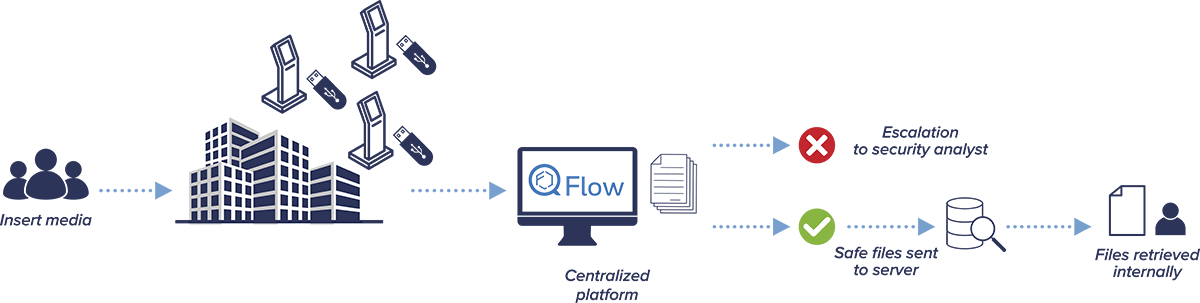
Simply plugging a USB key into an endpoint can give attackers a backdoor to your network
Monitoring the usage of removable media by each end user is inefficient/inconvenient
Traditional security measures may not suffice in defending against concealed threats